The Role of Human Factor in Spreading Malware
We all know that technology is made by people and for the people but bad technology is made by intelligent people to harm unaware people.
Have you ever thought that at the far end of a malware attack there are very sophisticated programmers and at the opposite end there are people who barely know what a virus is and don’t know how to operate a computer safely?
Malware usually does not target those who are in between, that is, people who are able to pay attention to how to stay safe online.
The human factor in cybersecurity plays a huge role and it is usually replaced by the expression “users’ education”. Companies are nowadays spending millions of dollars educating people about the risks involved in a cyber attack.
The target of a hacker is to find out where users are most vulnerable and access their network.
Read my articles about:
1- The first line of defense against ransomware for small businesses
2- If you are a residential user, learn what to do if you believe you have been hacked
3- Learn to take 7 proactive steps to protect your business in Westchester from Malware
THE PORTS OF ENTRY OF A MALWARE CAMPAIGN: LEARN WHERE HACKERS GAIN FOOTHOLD
- Believe it or not, a common attack is a telephone-oriented message. Hackers usually target the elderly and try to steal their banking or credit card information.
- Malicious urls: those type of infections target users who click on infected links that redirect them to bogus websites.
- Fake email messages: users are often tricked by fake emails reporting deliveries of products that are not real or credit card charges about subscription renewals that are simply not true. The user is worried and curious, clicks on the link and voila’: the rest is history.
- A business may have taken a proactive stance towards securing its network but if it grants access to a supplier who has a weaker security, the main business network can get compromised. An example of this type of attack took place in 2013 when a supplier was granted access to Target’s network.
As you can see, all these attacks were crafted by humans and targeted unaware humans.
Elements that define users’ risk: what type of human behavior determines that the user is at risk?
- Users’ Vulnerability: users become vulnerable when they click on something they should have not clicked on, or when they are unaware that a file may have been previously infected.
- Admin’s Incompetence: if an admin does not use a multi factor authentication or grants privilege to a user without being able to monitor that users’ behavior in the future, the admin acts naively and probably should not be the admin of a corporate network.
- Social Engineering: this attack leverages high-pressure environments that implement standard procedures. The standardization of processes that are never changed get into the eyes of hackers who exploit the lack of change in an organization that prefers automation. Automation gives chances to a hacker to learn weaknesses that are ready to be exploited.
- Improper Use: as the pandemic has forced millions of people to work from home, many users have admitted that they have used corporate devices to access personal accounts and that friends and family of employees have used devices originally assigned for business use.
- BYOD Devices: many smartphones sharing data of a corporate network have still not been secured with Mobile Device Management (MDM) policies. That can be an issue attributable to a business choice or to admins not having an holistic approach to security.
Ransomware is a such serious infection in that it can not only steal information from single users or corporations but it can also weaken the infrastructure of services used every day. Attacks are getting more sophisticated than ever: think about the ransomware installed in the IT admin tool Kaseya that spread across the networks Kaseya and other IT admin were managing. It took weeks to remediate the issue, patch software and networks to finally get rid of the infection. Hackers hide in the most unthinkable places and wait for their prey to come out: unbelievable.
Regular training that shows the latest tactics used by attacker is the best way to prevent networks from getting infected. As I often said, security is a process and not a one time task; the evolution of malware and its tactics should be used as a source of knowledge to educate system administrators and users on the dangers of a such fast moving environment, where scopes and targets can rapidly change.
Unfortunately, as computers are getting more secure and giving hard time to hackers, mobile threats are now on the rise. Hackers know that we all use more our mobile phones than computers to conduct business and make payments. Text messages with infected links can grant access to our contacts and send spam messages using our phones, unbeknownst to us. Persuasive messages range from package deliveries notifications to amazon purchases.
The role of the cloud is also to be mentioned here. Hackers are using the cloud to host their malware and to create suspicious applications that can collect users behaviors before crafting an attack. This type of spyware is very sophisticated and is usually defeated in a corporate environment by whitelisting only a restricted number of applications users can use. For residential users, however, things can be a little bit more complicated as their digital behavior is more permissive, but it will be sufficient to say at the moment that users should only download apps on their phones from the App Store and Google Play.
The pandemic has also made more difficult to track data loss prevention and in 2021 we have seen an increase in insider threats. This table provided by Proofpoint shows that protecting computers and laptop’s USB ports can prevent hackers from leaking information to muddy environments:
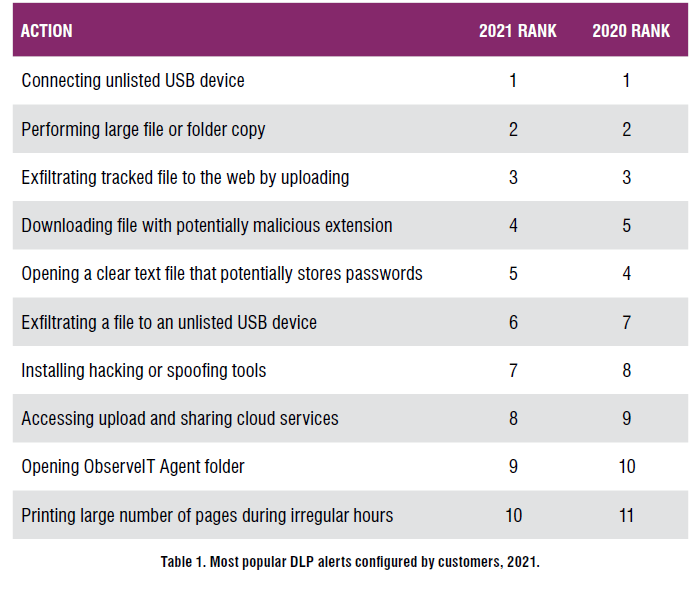
I have posted an article with an interesting video detailing instructions on how to secure USB devices on Windows 10, but the main requirement is that, in order to do that, the machine needs to run Windows 10 Pro and not the home version.
Human factors matter more than the technical aspects of an attack. Cyber criminals always look at what can be leveraged and access that can be exploited. Regular training can help users spot malicious emails and bad links contained in bogus websites.