Effective Ransomware Protection for Small Businesses
Ransomware is the worst type of malware users can ever encounter: while other types of viruses, even if they can steal your information, still allow you to operate your computer after the infection -and also potentially clean it-, ransomware locks down your machine and asks for money to restore it as it was before the infection. Ransomware leaves users with no choice: once your machine is hit by it, the only thing to do is to turn it off, because the infection can rapidly spread across other devices in your network.
If you run a small business, you should have your IT Department determine if your network is hit by ransomware.
Once the damage has been assessed, the business owner should never pay the ransom to have the files decrypted and restored, but he/she should take a proactive stance to avoid the incident happening again. And even if the ransom is paid, be aware that it’s not guaranteed that the files will be back as they were before.
As network and computer security is always a concern of mine, every time I visit my clients, I make them aware that a simple antivirus is not enough to protect against ransomware and that small business should take the following more holistic approach to better protect their networks:
- Keep the computers and servers operating systems always patched and up to date: as of this writing, please avoid using computers running Windows 7 and Windows 8.
- Make sure that your IT department runs backups that are taken out of the network and stored in a place that is not in the office where the main network is:
- The computers and servers should all run a good antimalware product such as the paid version of Malware bytes. If the machines do not run a third party anti ransomware product, please make sure that the IT department secures Windows 10 additional folders from ransomware as per picture below:
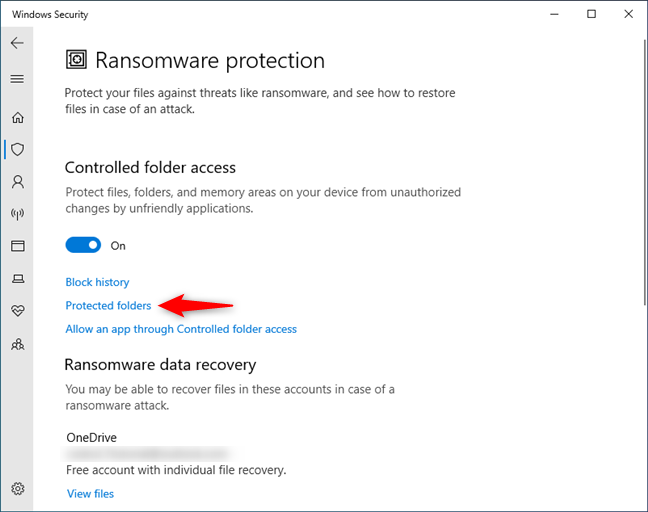
- Computers and servers’ files should also be backed up to cloud services such as Crashplan.
- User accounts should be all standard and non admin accounts; network administrators should apply the principle of “least privilege” when granting access to network resources and applications.
- Network administrators should never have user accounts credentials with the word “admin” but they should use a different bespoke word to handle admin accounts.
- As ransomware can also spread through infected email attachments, business owners should never run a business using a home gmail user account but he/she should invest in buying a bespoke domain and have email user accounts on Microsoft Exchange or Google Workspace platforms instead.
- Multi factor authentication should be used and enforced both for admins and regular users through Microsoft Authentication app and Google Authenticator apps installed on smartphones.
- Network Segmentation: if a computer or a server does not need to be shared with other users in the network, it should be placed in another network. More specifically, if the main computer network is on a 192.168.1.1 range of IP addresses, a firewall or a switch with VLAN capabilities should allow the IT department to create another network on a different set of IPs, such as 192.168.11.1, or 192.168.12.1, 13.1,14.1, subnets so that if an infection occurs in one network, it will not spread to another network. Network segmentation is the most useful task a smart IT department can accomplish to prevent and isolate infections.
- As per above, replace the main router with a firewall with etho0, eth1,eth2 network ports that allow the network to be split into several different networks.
- Educate users to be more proactive when visiting the web and clicking on emails containing infected links. IT departments should be involved not only in fixing things here and there, but also in showing users the risks involved in not paying attention to possible impersonated users or social engineering tactics.
If ransomware hits your network, the IT department should be authorized by the business owner to call the authorities before taking any action. After clearance from the authorities, all infected computers and servers should be formatted and operating systems should be reinstalled again from scratch. In a bulletproof network, users work together with IT people to establish not only trust but to engage in a constant flow of questions and answers where users learn more about what is dangerous and IT people can get a hold of users’ habits.